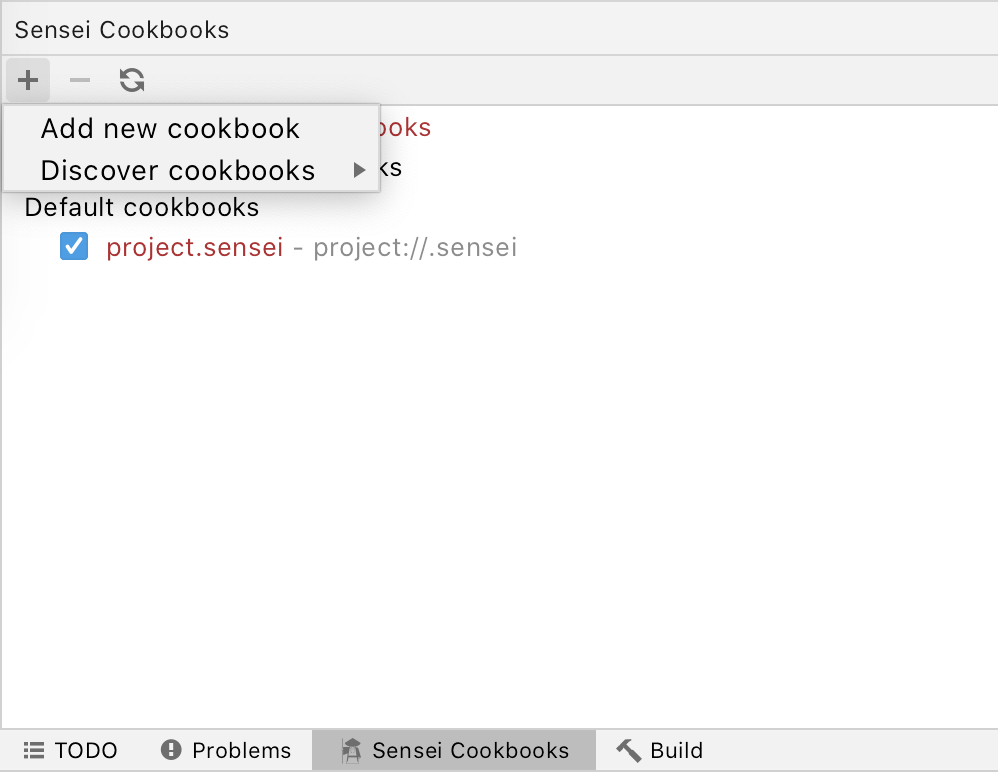
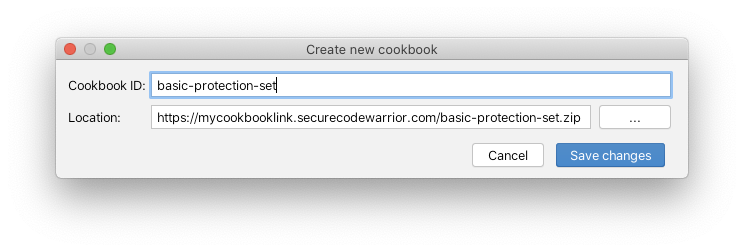
Basic |
|
Regex Injection
|
Use Pattern#quote to include untrusted input in regexes. |
java
|
error
|
securitySEI CERTJava basicinjectionOWASP Top 10
|
Database/Hibernate |
|
Hibernate: Missing transport-level security: No SSL for database connection
|
Use transport level security to connect to the database |
xml
|
warning
|
databasesecurityHibernateframework specificOWASP Top 10TLS
|
Database/JPA |
|
Injection - SQL Injection in JPA: EntityManager#createNativeQuery
|
Avoid SQLi by using parameterized queries, instead of string concatenation with untrusted input |
java
|
error
|
securityJPAinjectionSQLOWASP Top 10
|
|
Injection - SQL Injection in JPA: EntityManager#createQuery
|
Avoid SQLi by using parameterized queries, instead of string concatenation with untrusted input |
java
|
error
|
securityJPAinjectionSQLOWASP Top 10
|
Database/MongoDB |
|
MongoDB: _id NoSQL Injection
|
Do not use string concatenation in where filters |
java
|
error
|
securityNoSQLframework specificMongoDBinjectionOWASP Top 10
|
Database/SQL |
|
Injection: Avoid SQL Injection: Use Parameterized Queries (PreparedStatement)
|
Could lead to SQL Injection |
java
|
error
|
securitySEI CERTbasic protection setinjectionSQLOWASP Top 10
|
|
Injection: Avoid SQL Injection: Use Parameterized Queries (Statement)
|
Could lead to SQL Injection |
java
|
error
|
securitySEI CERTbasic protection setinjectionSQLOWASP Top 10
|
Dependencies/Maven |
|
Vulnerable Log4j dependency - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j dependency - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
xml
|
error
|
Apache MavenLog4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
|
Vulnerable Log4j version property - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j version property - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
xml
|
error
|
Apache MavenLog4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
Expression Language |
|
Input Validation: Avoid Expression Language Injection: Do not evaluate expressions controlled by user input (javax)
|
Could lead to Expression Language Injection |
java
|
error
|
expression languagesecurityinjectionOWASP Top 10
|
LDAP |
|
Data: Injection: Parameterize LDAP Filters: DirContext#search
|
Could lead to LDAP Injection |
java
|
error
|
securityLDAPinjectionOWASP Top 10
|
Logging/Log4J |
|
Vulnerable Log4j version - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j version - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
javakotlin
|
error
|
Log4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
Logging/Logger |
|
Untrusted input in logging
|
Prevent log injection by filtering untrusted input |
java
|
info
|
securityOWASP Top 10framework specificloggingLoggerinjection
|
Logging/SLF4J |
|
SLF4J Logging: enforce usage of placeholders in the messages
|
Do not concatenate untrusted data in the message string, instead use placeholders ( '{}' ) |
java
|
marked_information
|
securitylogginginjectionOWASP Top 10SLF4Jframework specific
|
Mobile/Android SDK/SQLite |
|
SQL Injection: SQLiteDatabase#execSQL
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteDatabase#query - 1st parameter
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteDatabase#query - 2nd parameter
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteDatabase#query - 3rd parameter
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteDatabase#query - 5th parameter
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteQueryBuilder appendWhere
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteQueryBuilder compileStatement
|
This query could lead to SQL injection |
java
|
error
|
securityframework specificmobileinjectionAndroidSQLOWASP Top 10
|
|
SQL Injection: SQLiteQueryBuilder compileStatement Compliant
|
SQL Injection: SQLiteQueryBuilder compileStatement - Compliant |
java
|
compliant
|
securityframework specificmobileinjectionAndroidSQLAndroid security setOWASP Top 10
|
|
SQL Injection: SQLiteQueryBuilder#buildQuery
|
This method is vulnerable to SQL injection. Consider writing the query instead of relying on builders. |
java
|
error
|
securityframework specificmobileinjectionSQLAndroidOWASP Top 10
|
Neo4J |
|
Spring Data Neo4jClient#query is vulnerable to injections
|
Spring Data Neo4jClient#query is vulnerable to injections |
java
|
error
|
securityNeo4jframework specificOWASP Top 10injectionSpring Data
|
Spring/Boot |
|
Session configuration: Cookies: Configure HttpOnly flag
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
Springsecurityframework specificwebSpring BootOWASP Top 10
|
|
Session configuration: Cookies: Configure Secure flag
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
Springsecurityframework specificwebSpring BootOWASP Top 10
|
|
Session configuration: Cookies: Set HttpOnly flag to true
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
Springsecurityframework specificwebSpring BootOWASP Top 10
|
|
Session configuration: Cookies: Set Secure flag to true
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
Springsecurityframework specificwebSpring BootOWASP Top 10
|
Spring/Core |
|
Input Validation: Avoid Spring Expression Language Injection: Do not evaluate expressions controlled by user input (ExpressionParser)
|
Could lead to Spring Expression Language Injection |
java
|
error
|
expression languageSpringSpring Coresecurityframework specificinjectionOWASP Top 10
|
Spring/Data/JDBC |
|
Input Validation: Avoid JDBC Injection: Bind variables in prepared statements: Two parameters
|
Could lead to JDBC Injection |
java
|
error
|
SpringsecuritySpring Dataframework specificinjectionSQLOWASP Top 10
|
|
Input Validation: Avoid JDBC Injection: Bind variables in prepared statements: single parameter
|
Could lead to JDBC Injection |
java
|
error
|
SpringsecuritySpring Dataframework specificinjectionSQLOWASP Top 10
|
Spring/Security |
|
Authentication: Username Enumeration: avoid UsernameNotFoundException
|
Avoid throwing a UsernameNotFoundException as it could lead to username enumeration |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Authentication: Username Enumeration: setHideUserNotFoundExceptions should be set to true
|
Prevent enumeration by not throwing an exception that reveals the existence of the username |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Security Misconfiguration: Clickjacking protection: Disabled Header - frameOptions()
|
Disabling Spring Security default headers makes the application vulnerable to clickjackin |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityClickjackingOWASP Top 10
|
|
Security Misconfiguration: Content sniffing protection
|
Prevent MIME sniffing by disabling contentTypeOptions |
java
|
error
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Security Misconfiguration: Disabled Headers
|
Disabling Spring Security's default headers makes the application vulnerable |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Security Misconfiguration: EnableWebSecurity with Debug enabled
|
The debug parameter on EnableWebSecurity should not be hardcoded to true |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
Spring/Security/CSRF |
|
CSRF: Disabled CSRF protection (AbstractHttpConfigurer)
|
Disabling Spring Security's CSRF protection makes the application vulnerable |
java
|
error
|
Springsecurityframework specificwebSpring SecurityCSRFOWASP Top 10
|
|
CSRF: Disabled CSRF protection (HttpSecurity)
|
Disabling Spring Security's CSRF protection makes the application vulnerable |
java
|
error
|
Springsecurityframework specificwebSpring SecurityCSRFOWASP Top 10
|
|
Security Misconfiguration: Disabled Security Settings: CookieCsrfTokenRepository#withHttpOnlyFalse
|
Make sure to set HttpOnly to true to protect against CSRF or remove it |
java
|
error
|
Springsecurityframework specificwebSpring SecurityCSRFOWASP Top 10
|
Spring/Security/HTTPS |
|
Secure Transport: use RequiresSecure to enforce HTTPS
|
Serve requests over HTTPS instead of unencrypted HTTP |
java
|
error
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Secure Transport: use RequiresSecure to enforce HTTPS on all paths
|
Enforce HTTPS on all requests, not just on a selected number |
java
|
warning
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Security Misconfiguration: Disable Security Features - HSTS
|
Enforce HSTS protection against vulnerabilities over HTTP |
java
|
error
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Security Misconfiguration: HSTS - includeSubDomains
|
Include subdomains in the HSTS domain |
java
|
error
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
|
Should use requiresSecure
|
Use of HTTP instead of HTTPS is insecure |
java
|
error
|
Springsecurityframework specificwebSpring SecurityOWASP Top 10
|
Spring/Security/XSS |
|
Security Misconfiguration: XSS protection: Add CSP header - XXssConfig
|
Add a CSP header for additional protection agains XSS and data injection |
java
|
info
|
Springsecurityframework specificSpring SecuritywebXSSOWASP Top 10
|
|
Security Misconfiguration: XSS protection: Add CSP header - xssProtection
|
Add a CSP header for additional protection agains XSS and data injection |
java
|
info
|
Springsecurityframework specificSpring SecuritywebXSSOWASP Top 10
|
|
Security Misconfiguration: XSS protection: Disabled Header - block()
|
Protection against XSS is better done by blocking the content instead of filtering it |
java
|
warning
|
Springsecurityframework specificSpring SecuritywebXSSOWASP Top 10
|
|
Security Misconfiguration: XSS protection: Disabled Header - disable()
|
Do not disable Spring Security's built-in XSS protection |
java
|
warning
|
Springsecurityframework specificSpring SecuritywebXSSOWASP Top 10
|
|
Security Misconfiguration: XSS protection: Disabled Header - xssProtectionEnabled()
|
Do not disable Spring Security's built-in XSS protection |
java
|
warning
|
Springsecurityframework specificSpring SecuritywebXSSOWASP Top 10
|
Spring/Web/Cookies |
|
Session configuration: Cookies: Configure Secure flag
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
Springsecurityframework specificwebSpring WebOWASP Top 10
|
|
Session configuration: Cookies: Set HttpOnly flag to true
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
Springsecurityframework specificwebSpring WebOWASP Top 10
|
|
Session configuration: Cookies: Set Secure flag to true
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
Springsecurityframework specificwebSpring WebOWASP Top 10
|
Spring/XML |
|
Injection: XXE: Jaxb2Marshaller#setProcessExternalEntities set to true
|
Prevent XXE by disabling the processing of external entities |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Injection: XXE: Jaxb2Marshaller#setSupportDtd set to true
|
Prevent XXE by disabling DTDs |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Injection: XXE: Jaxb2RootElementHttpMessageConverter#setProcessExternalEntities set to true
|
Prevent XXE by disabling the processing of External Entities |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Injection: XXE: Jaxb2RootElementHttpMessageConverter#setSupportDtd set to true
|
Prevent XXE by disabling DTDs |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Injection: XXE: SourceHttpMessageConverter#setProcessExternalEntities set to true
|
Prevent XXE by disabling the processing of External Entities |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Injection: XXE: SourceHttpMessageConverter#setSupportDtd set to true
|
Prevent XXE by disabling DTDs |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
|
Input Validation: Avoid XXE: Use automatically protected source types
|
Could lead to XXE |
java
|
error
|
SpringsecurityXXEframework specificSpring XMLOWASP Top 10
|
Web/Apache/Cookies |
|
Session configuration: Cookies: Configure HttpOnly flag
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
securitywebApache ShiroOWASP Top 10
|
|
Session configuration: Cookies: Configure Secure flag
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
securitywebApache ShiroOWASP Top 10
|
|
Session configuration: Cookies: Set HttpOnly flag to true
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
securitywebApache ShiroOWASP Top 10
|
|
Session configuration: Cookies: Set Secure flag to true
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
securitywebApache ShiroOWASP Top 10
|
Web/Apache/Mail |
|
Email: Disabled SSL Server Identity check
|
When sending an email, the setSSLCheckServerIdentity has been set to false |
java
|
error
|
securityApache CommonswebemailOWASP Top 10
|
|
Email: Disabled SSL on Connect
|
When sending an email, SSL has been disabled on connection |
java
|
error
|
securityApache CommonswebemailOWASP Top 10
|
Web/Cookies |
|
Session configuration: Cookie: Configure HttpOnly flag
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
securitywebOWASP Top 10
|
|
Session configuration: Cookies: Configure Secure flag
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
securitywebOWASP Top 10
|
|
Session configuration: Cookies: Set HttpOnly flag to true
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
securitywebOWASP Top 10
|
|
Session configuration: Cookies: Set Secure flag to true
|
Prevent a cookie being sent over unencrypted HTTP by setting the Secure flag to true |
java
|
error
|
securitywebOWASP Top 10
|
|
Session configuration: HttpCookie: Configure HttpOnly flag
|
Prevent client-side scripts from accessing the cookie by setting the HttpOnly flag to true |
java
|
error
|
securitywebOWASP Top 10
|
Web/TLS |
|
TLS: Disabled Certificate validation
|
The verify method has been overridden, and always returns true |
java
|
warning
|
securitywebTLSOWASP Top 10
|
|
TLS: Weak Encryption: Insecure Version
|
Could lead to Data Exposure |
java
|
error
|
securitywebTLSOWASP Top 10
|
|
TLS: Weak Encryption: Outdated Version
|
Could lead to Data Exposure |
java
|
warning
|
securitywebTLSOWASP Top 10
|
|
X509: Disabled validation in TrustManager
|
A TrustManager has overridden the getAcceptedIssuers method, and only returns null. |
java
|
warning
|
securitywebTLSOWASP Top 10
|
XML/XXE |
|
XXE: DocumentBuilderFactory: Add missing feature dissallow-doctype-decl
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature external-parameter-entities
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature load-external-dtd
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature setExpandEntityReferences
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature setXIncludeAware
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Set features to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Set features to true
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Setters to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: Set missing secure processing feature
|
Could lead to XXE |
java
|
error
|
OWASP Top 10XMLXXEbasic protection setsecurity
|
|
XXE: Set secure processing feature to true
|
Could lead to XXE |
java
|
error
|
securityXMLbasic protection setXXEOWASP Top 10
|
|
XXE: XMLInputFactory: Add IS_SUPPORTING_EXTERNAL_ENTITIES feature
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: XMLInputFactory: Add SUPPORT_DTD feature
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: XMLInputFactory: Set features to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
YAML |
|
Injection: Avoid Code Injection: Use SafeConstructor: 1st argument of type Constructor
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|
|
Injection: Avoid Code Injection: Use SafeConstructor: arguments, but no Constructor argument
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|
|
Injection: Avoid Code Injection: Use SafeConstructor: no arguments
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|