Crypto/Cipher |
|
Crypto: Cipher: Insecure Asymmetric Cryptographic Algorithm
|
This cryptographic algorithm is not recommended |
java
|
error
|
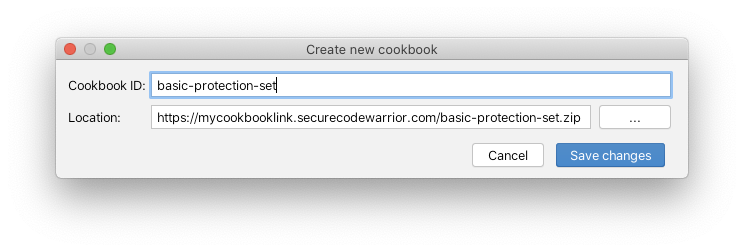
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use strong symmetric cryptographic algorithm
|
Could lead to cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use strong symmetric cryptographic algorithm (Untrusted)
|
Alowing untrusted input to determine the encryption algorithm could lead to cryptographic weakness. |
java
|
warning
|
securitybasic protection set
|
|
Data Protection - Secure Data Storage: Avoid data exposure: Use Cipher instead of NullCipher
|
Could lead to data exposure |
java
|
error
|
securitybasic protection set
|
Crypto/KeyAgreement |
|
Crypto: KeyAgreement: Guide on Approved Cryptographic Algorithm
|
This cryptographic algorithm is not recommended |
java
|
marked_information
|
securitybasic protection set
|
|
Crypto: KeyAgreement: Insecure Cryptographic Algorithm
|
This cryptographic algorithm is insecure |
java
|
error
|
securitybasic protection set
|
Crypto/KeyGeneration |
|
Crypto: KeyPair Generation: Approved Standard Cryptographic Algorithm
|
This cryptographic algorithm is not recommended |
java
|
error
|
securitybasic protection set
|
|
Crypto: KeyPair Generation: Insecure Cryptographic Algorithm
|
This cryptographic algorithm is insecure |
java
|
error
|
securitybasic protection set
|
|
Crypto: KeyPair Generation: Non Standard Cryptographic Algorithm
|
This cryptographic algorithm is not recommended |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid brute forcing: Use sufficiently long key sizes: keyGenerator
|
Could lead to brute forcing or other cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate key pair generation algorithm: insecure
|
Could lead to cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate key pair generation algorithm: not recommended
|
Could lead to cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate secret key generation algorithm: DES family
|
Could lead to brute forcing or other cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate secret key generation algorithm: Hmac family
|
Could lead to brute forcing or other cryptographic weakness |
java
|
warning
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate secret key generation algorithm: Other algorithms
|
Could lead to brute forcing or other cryptographic weakness |
java
|
marked_information
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate secret key generation algorithm: insecure SecretKeyFactory
|
Could lead to cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use appropriate secret key generation algorithm: other SecretKeyFactory
|
Could lead to cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use sufficiently long key sizes: keyGenerator bad value
|
Could lead to brute forcing or other cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use sufficiently long key sizes: keyPairGenerator
|
Could lead to brute forcing or other cryptographic weakness |
java
|
error
|
securitybasic protection set
|
|
Data Protection - Cryptography: Avoid cryptographic weakness: Use sufficiently long key sizes: keyPairGenerator bad value
|
Could lead to brute forcing or other cryptographic weakness |
java
|
error
|
securitybasic protection set
|
Crypto/Signatures |
|
Crypto: Signature: Approved Hashing Algorithm
|
This hashing algorithm is not recommended for cryptographic use |
java
|
marked_information
|
securitybasic protection set
|
|
Crypto: Signature: Insecure Hashing Algorithm
|
This hashing algorithm is not recommended for cryptographic use |
java
|
error
|
securitybasic protection set
|
|
Crypto: Signature: Non Standard Hashing Algorithm
|
This hashing algorithm is not recommended for cryptographic use |
java
|
warning
|
securitybasic protection set
|
Database/SQL |
|
Injection: Avoid SQL Injection: Use Parameterized Queries (PreparedStatement)
|
Could lead to SQL Injection |
java
|
error
|
securitySEI CERTbasic protection setinjectionSQLOWASP Top 10
|
|
Injection: Avoid SQL Injection: Use Parameterized Queries (Statement)
|
Could lead to SQL Injection |
java
|
error
|
securitySEI CERTbasic protection setinjectionSQLOWASP Top 10
|
Dependencies/Maven |
|
Vulnerable Log4j dependency - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j dependency - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
xml
|
error
|
Apache MavenLog4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
|
Vulnerable Log4j version property - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j version property - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
xml
|
error
|
Apache MavenLog4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
Logging/Log4J |
|
Vulnerable Log4j version - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105
|
Vulnerable Log4j version - Log4Shell/CVE-2021-44228/CVE-2021-45046/CVE-2021-45105 |
javakotlin
|
error
|
Log4jOWASP Top 10SLF4Jbasic protection setframework specificinjectionloggingsecurity
|
XML/XXE |
|
XXE: DocumentBuilderFactory: Add missing feature dissallow-doctype-decl
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature external-parameter-entities
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature load-external-dtd
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature setExpandEntityReferences
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Add missing feature setXIncludeAware
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Set features to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Set features to true
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: DocumentBuilderFactory: Setters to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: Set missing secure processing feature
|
Could lead to XXE |
java
|
error
|
OWASP Top 10XMLXXEbasic protection setsecurity
|
|
XXE: Set secure processing feature to true
|
Could lead to XXE |
java
|
error
|
securityXMLbasic protection setXXEOWASP Top 10
|
|
XXE: XMLInputFactory: Add IS_SUPPORTING_EXTERNAL_ENTITIES feature
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: XMLInputFactory: Add SUPPORT_DTD feature
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
|
XXE: XMLInputFactory: Set features to false
|
Could lead to XXE |
java
|
error
|
securityXXEbasic protection setOWASP Top 10
|
YAML |
|
Injection: Avoid Code Injection: Use SafeConstructor: 1st argument of type Constructor
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|
|
Injection: Avoid Code Injection: Use SafeConstructor: arguments, but no Constructor argument
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|
|
Injection: Avoid Code Injection: Use SafeConstructor: no arguments
|
Could lead to Remote Code Execution |
java
|
error
|
securitybasic protection setinjectionYAMLOWASP Top 10
|