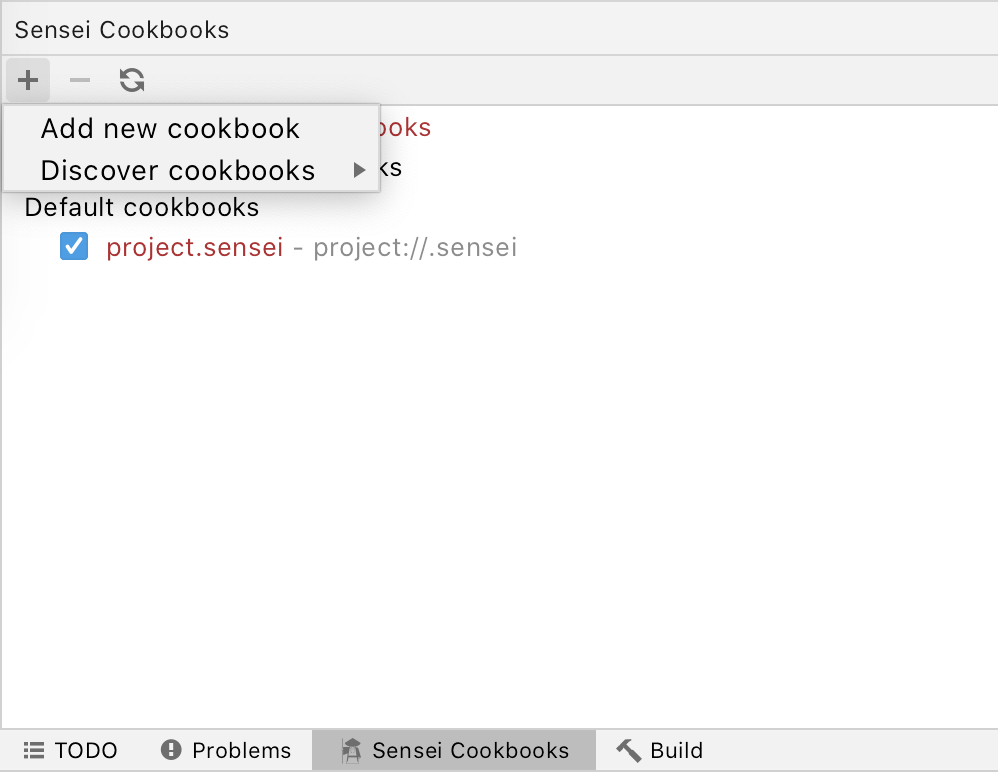
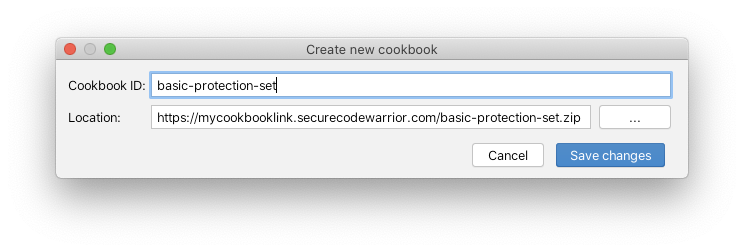
Cookbook Name:
Android Security Set
Description:
Recipes created from security recommendations in the official Android documentation (https://developer.android.com/), including checks for the manifest file, injection vulnerability, configuration and storage.
Owner:
Secure Code Warrior
Number of Recipes:
19
Markdown badge: